This post is also available in:
 Nederlands (Dutch)
Nederlands (Dutch)

ARAMA TECH SERVICES
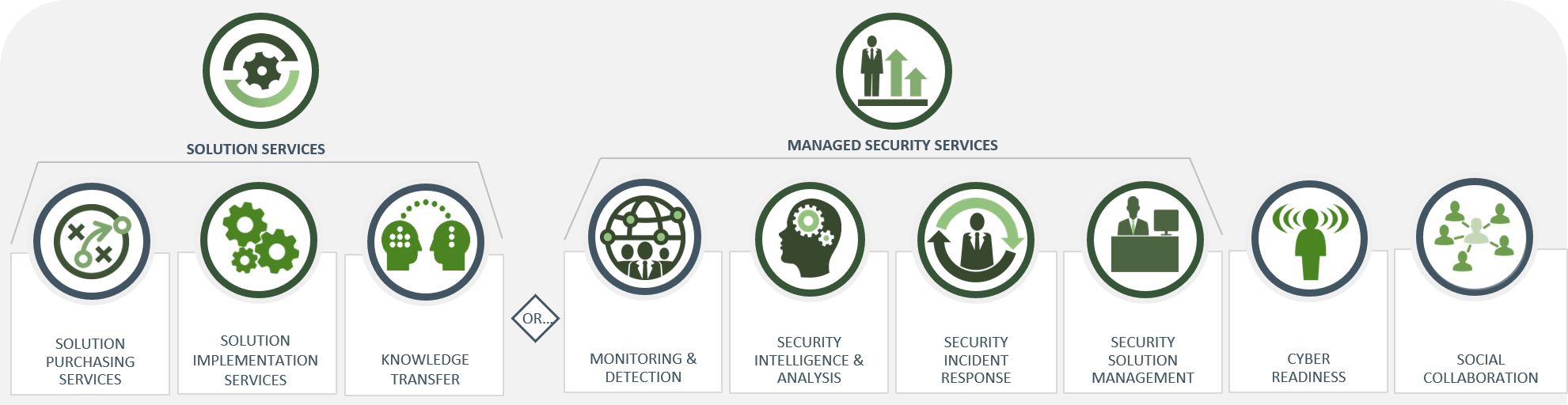
ARAMA TECH offers clients and partners Managed Security Services (MSS) For INCIDENT RESPONSE & ORCHESTRATION, SIEM, INTRUSION DETECTION & PREVENTION, ADVANCED THREAT PROTECTION, DATA LOSS PREVENTION, WEB & EMAIL SECURITY, SERVER & ENDPOINT PROTECTION, CASB solutions for organizations would like to use these technologies but that but do not (yet) have the required teams or the required level of knowledge to manage and operate these solutions independently. This partnership offers the customer the opportunity to focus on their core activities and core competencies, and to be assured of protection against cyber attacks.
ARAMA TECH MSS offers a wide range of services, from a complete CloudSOC where customers outsource Security operations Center activities to ARAMA TECH to separate services such as active hunting for threats and forensic investigations of Incidents when a breach has occurred (ARAMA TECH Advanced Threat Services). We also manage and protect mobile devices as part of our managed Security Services.
For information on any of the services of ARAMA TECH MSS please use the contact form.
IMPLEMENTATION SERVICES
Technical installation and Business implementation of the most important Processes, Procedures and Products in the field of:
- Incident Response & Orchestration
- Policy & Compliance Management (ISO/Cobit processes and management measures)
- Data Protection Program (CASB, DLP)
- Security Intelligence (Advanced SIEM )
- Network, server and endpoint security
- Enterprise Mobile Security
- Advanced Threat Protection
- Enterprise Vulnerability Management
ARAMA TECH offers improved Best practices based on industry standards in line with laws and regulations and business objectives.
SECURITY ASSESSMENT SERVICES
Next Generation Security Assessment methodologies provide the necessary information to pro-actively control information security risks by gaining insight into the maturity level of your Security organization and combining asset Business context, actionable threat intelligence and security test results.
SECURITY HEALTH ASSESSMENT Measures the maturity level of your organization compared with frameworks and controls of CobiT5, ISO 27002 and ISF Standard of Good Practice (SoGP).
Enterprise VULNERABILITY MANAGEMENT includes advanced Security testing services such as static Code analysis, VULNERABILITY testing and penetration testing of networks, Web applications and mobile applications.
TRAINING ACADEMY
Employees are the “attack VECTOR”
ARAMA TECH E-Learning has been set up to provide the right information to employees so the will be able to efficiently identify attacks and incidents and to be able to identify and alert them, rather than become targets for hackers. At the same time, employees learn to work more consciously safer in a simple and fun way!
Some challenges:
- Involving employees in security and their role in protecting data is a challenge. Most employees do not think it is their “responsibility”, when in fact it is everyone’s responsibility.
- Employees are not sufficiently aware of the risks. They think, for example, that they do not fall easily in phishing traps, but in fact that is the case!
- Security training must be continually updated.
- There is no proven set of training manuals that addresses the “people problem”.
- Security and data protection is usually not the primary focus of employees.
- Security training is another training that takes up valuable working time.
ARAMA TECH E-LEARNING Features
Short training modules, 10 – 15 minutes
- Effectively use the attention arc of employees
- Limited investment in business time for training
- Easily compile a program of different modules.
- Creating repeated attention to security issues
Keep it simple
- What an employee should know and do
- Don’t give too much information in 1 time
The modules are customizable
- The modules can be made in the customer’s house style if desired.
- Support for 24 + languages
- Training content can be made customer-specific if desired
Different Models
- Learning Management System (LMS) of the customer
- ARAMA TECH Hosted Cloud LMS
Available MODULES
- Comply with laws and regulations
- GDPR
- Privacy
- Classifying information
- Dealing with confidential information
- Reporting incidents
- Data leakage
- Phishing
- Malware
- Social Engineering
- Protecting Customer Data
- Business use of Internet
- Business use of e-mail
- Social networking
- Cloud Computing
- Use mobile devices
- Use of public hotspots
- Physical access control and visitors
- Working with 3rd Parties
- Working at home
- Working in public environments
- Information security when traveling
- Loss and theft of mobile devices
- Passwords
- Clean desk and clean office
- … we will continue to add new themes…
ARAMA TECH MANAGED SECURITY SERVICES
ARAMA TECH MSS offers organizations that do not (yet) have the required teams or the required level of knowledge to manage these solutions independently and to operate these technologies. This partnership offers the customer the opportunity to focus on their core activities and core competencies, and to be assured of protection against cyber attacks.
ARAMA TECH offers customers and partners Managed Security Services (MSS) for:
- Incident Response & Orchestration
- Security Incident Event Monitoring (SIEM)
- Data Loss Prevention & CASB
- Intrusion Detection & Prevention
- Advanced Threat Services
- Network, Server & Endpoint Protection
- Enterprise Mobile Security
- Web- and Email Security
HYBRID MANAGED SERVICES
HYBRID MANAGED SECURITY SERVICES is characterized by the installation of a strong knowledge transfer element with a gradual thinking towards the internal organization of customers within a certain agreed time period. This provides a flexible service that allows an organization to grow in capacity and knowledge at their own pace.
FULL MANAGED SERVICES
FULL MANAGED SECURITY SERVICES takes care of organization fully and invested first line management and security Operations in the chosen security areas and solutions and the first line response to incidents at ARAMA TECH. Security experts monitor, detect, analyze and take appropriate actions on security events and incidents, in line with the policies and processes surrounding incident management of the customer. ARAMA TECH also offers full services for application & functional management of your Security products.
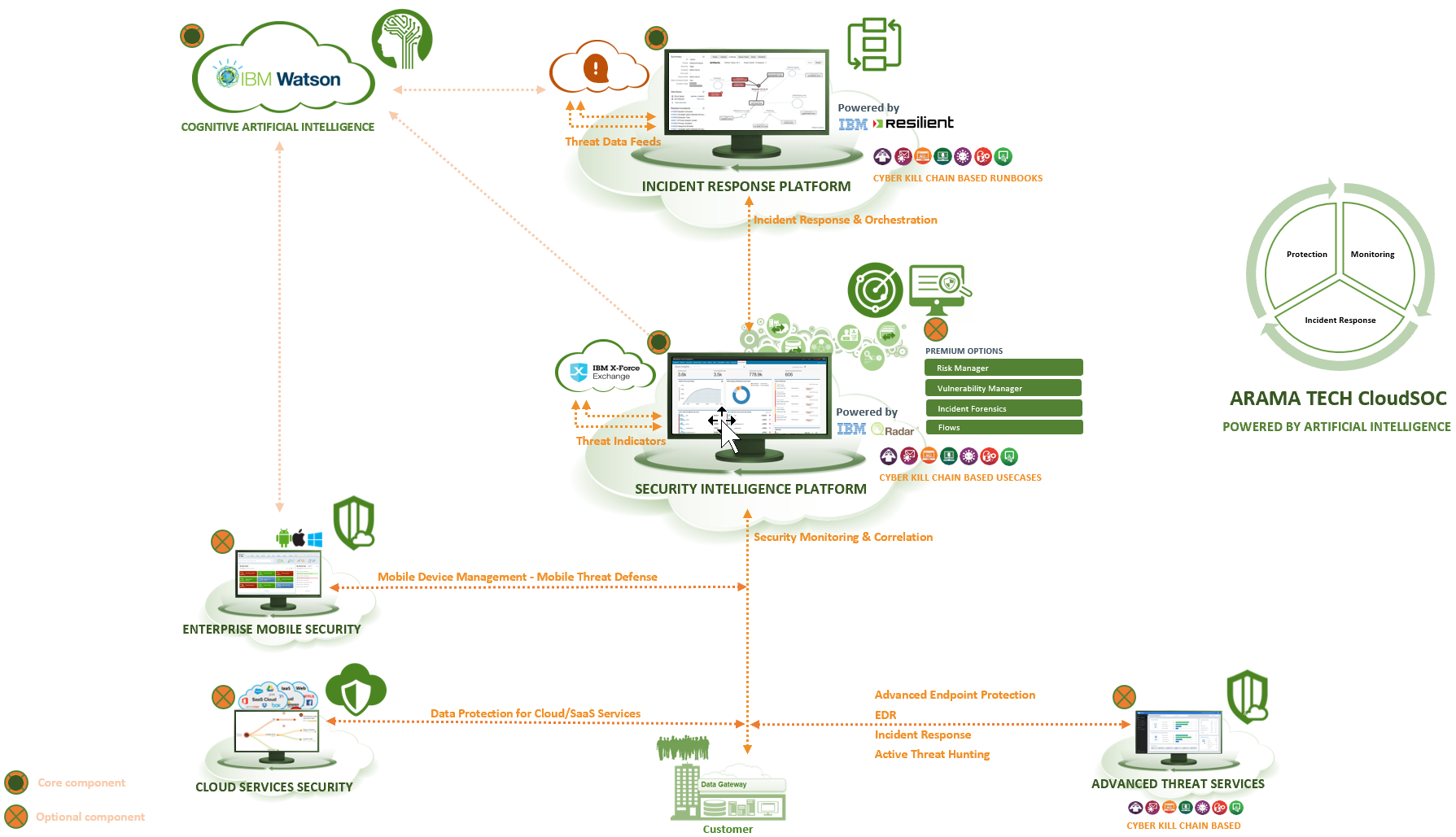
ARAMA TECH INCIDENT RESPONSE PLATFORM
Respond faster, more efficiently, and more intelligently to Security incidents with the IBM Resilient incident Response Platform.
ARAMA TECH Incident Response Platform (IRP) is a service that uses the IBM Resilient Incident Response Platform (IRP) to create a central hub that enables ARAMA TECH to provide the full Response Response Process for connected customers and perform a quicker and more intelligent response and mitigation. ARAMA TECH Incident Response Platform offers a full Incident response orchestration about people, process and technology.
- People: ARAMA TECH IRP facilitates collaboration between ARAMA TECH CloudSOC and the client (e.g. HR, Security, compliance, IT Operations and Management).
- Process: ARAMA TECH IRP offers dynamic Playbooks built on NIST/CERT/SANS standards, but is easily customizable on the client’s SOPs.
- Technology:the ARAMA TECH IRP Resilient Incident Response Platform is an open and agnostic platform that integrates with the customer’s security infrastructure and provides a central hub for incident response. It integrates for example with SIEMs, firewalls, proxies, AV and Endpoint Protection Solutions, Vulnerability Management Solutions, ITSM solutions, etcetera. This allows the customer to manage their security incidents in one central platform rather than in the many different technologies.
ARAMA TECH IRP helps customers to:
- strengthen their security team by creating a central hub for managing, automating and orchestrating Security Incident Response processes.
- alignment of people, processes and technology for incident response.
- connect and optimize all their security investments – and make the ROI of their security investments measurable.
![]() PROFESSIONAL SERVICES: IBM Resilient Implementation Services
PROFESSIONAL SERVICES: IBM Resilient Implementation Services
ARAMA TECH has the knowledge and proven experience to implement the IBM Resilient Incident Response Platform in the most complex environments, in a project-based manner. Components of the implementation include:
- Sizing and scoping of the required solution.
- Drawing up a clear project plan, implementation plan and operational guidelines.
- SOC process analysis and optimizing them.
- Drafting of technical architecture and design designs.
- Installing the required Resilient platform and provisioning Backup & Recovery.
- Building incident frameworks based on methodologies such as the Cyber Kill Chain and MITRE.
- Building dynamic Runbooks in line with the monitoring use cases and Incident Response procedures.
- Building integrations with existing solutions such as SIEM, AV, firewalls, ITSM solutions, etcetera.
- Provision of reports and other functional requirements that customers may have.
- Training and knowledge transfer to the organization.
- Etcetera …
![]() PROFESSIONAL SERVICES: IBM Resilient Platform Management
PROFESSIONAL SERVICES: IBM Resilient Platform Management
ARAMA TECH has the knowledge and proven experience to efficiently manage your IBM Resilient platform and connections with other solutions and complete additional support tasks. ARAMA TECH operates a professional service desk, accessible via a secure connection and is only accessible to authorized persons of the customer. ARAMA TECH uses the IBM Resilient Incident Response platform and, in addition to security Incident response management and orchestration, has also developed other functionalities within the IBM Resilient platform for IT Service management such as disturbances, functionality requests, problems and modification requests.
ARAMA TECH uses a Social collaboration Platform, where a digital work environment is built where the direct interaction between employees internally, but also with customers and partners, has become many times more efficient. This increases and strengthens the added value of ARAMA TECH for customers and partners. For each managed Security Services customer, a community is set up on this Social collaboration Platform where the community members can have interactions with colleagues and ARAMA TECH specialists in a protected and secure environment for sharing of experiences, where the knowledge base and information such as release notes and other relevant product information is published, notice about online events such as WebEx presentations and much more.
ARAMA TECH builds a dynamic Web Form portal per customer, including the supporting processes, for requesting things like adding Resilient users, requesting new runbooks and modifying existing runbooks. Tasks within the IBM Resilient platform management include:
- Application Management
- General monitoring of the platform
- Continuity monitoring
- Performance Monitoring
- Adaptive Management (updates and patches, etc.)
- Additive Management (upgrades, etc.)
- Corrective Management (correction of disturbances, etc.)
- Functional management
- Access control
- User Management
- License Management
- Other tasks
- IBM Resilient Change Management
- Coordination with IBM Support
- Coordination with internal and/or hosting and platform management
- Advising on Security Incident Response Strategies
- Etcetera …
![]() PROFESSIONAL SERVICES: IBM Resilient Runbook Management
PROFESSIONAL SERVICES: IBM Resilient Runbook Management
ARAMA TECH has the knowledge and proven experience to efficiently build the IBM Resilient runbooks New, adapt existing runbooks and conduct general management and maintenance of the runbooks as used by the customer. For every runbook, ARAMA TECH Runbook designs and maintains them so that they can be efficiently secured in the organization. Any change to a runbook is recorded by means of a clear process and after its approval is carried out based on an approved Runbook Design.
ARAMA TECH SECURITY MONITORING & INTELLIGENCE
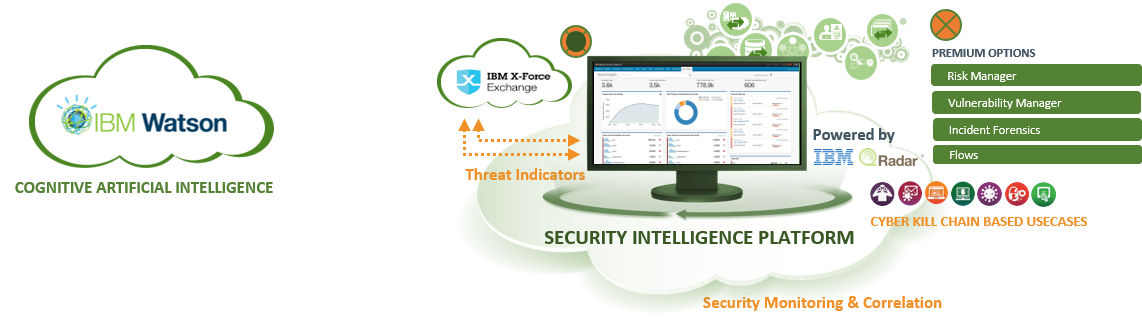
ARAMA TECH Security Intelligence Platform is a network security intelligence and Analytics service that helps detect cyber Security attacks and breaches so that connected customers can take action before significant damage has been inflicted and can immediately respond to the loss of critical data if it occurs.
Security Information and Event Management (SIEM) collects and analyzes central log and network flow data in even the most distributed environments and provides action-oriented insight into threats. Using advanced analytics, the solution searches billions of events a day for unusual and malicious activities, identifies and groups related events and generates prioritized alerts of only the most critical Threats.
ARAMA TECH Security Intelligence Platform is a cloud-based service that allows the customer to focus on controlling unusual conditions and solving the most important assets, instead of purchasing and deploying technology Components. Customers can start using the ARAMA TECH Security Intelligence Platform based on a monthly cost model and fast upscaling as needed.
ARAMA TECH CLOUDSOC is a network and cloud/SaaS Services Security Intelligence and analytics service that can assist you in detecting cyber security attacks and network and Cloud data breaches, conducting efficient Incident Response and protecting critical servers, applications and data when using Cloud/SaaS services. A cloud-based service that has minimal impact on your organization’s infrastructure during roll-out and operation, maximum efficiency by using a standard framework for identifying incident types and managing security Incidents. ARAMA TECH CLOUDSOC is modular and provides a tailor-made solution for your organization on a pay per use, monthly cost model. We would like to talk about this unique proposition!
ARAMA TECH ADVANCED THREAT SERVICES
ARAMA TECH Advanced Threat Services supports customers in addressing advanced threats or investigating the source and working methods in case of incidents. This service is additional to existing security solutions and provides deeper insight into malicious activity on endpoints and provides insight into the behavior of the attacker so that repetition can be avoided.
Pre Incident activities include continuous monitoring and active threat hunting, actively searching for traces and patterns that may indicate an attack. This rolls out the solution across all endpoints and starts active monitoring, separate from security solutions such as endpoint protection systems. The lightweight agent has hardly any impact on the performance of the endpoints.
Post-Incident activities include forensic investigations into the root cause of an incident, intuitively visualizing the attack chain, shutting down the source of the attack and responding to an incident by isolating the affected Endpoint. These activities are even possible if the customer is not yet using ARAMA TECH Advanced Threat Services.
ARAMA TECH Advanced Threat Services uses multiple threat intelligence feeds to enrich the incidents and research techniques.
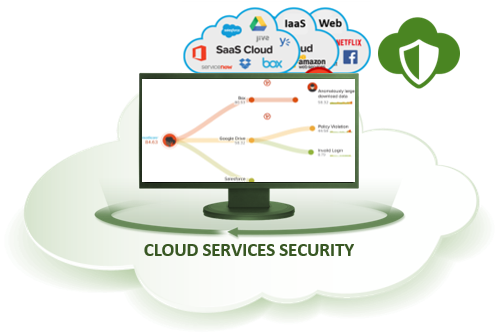
ARAMA TECH CLOUD SERVICES SECURITY
ARAMA TECH Cloud Services Security supports organizations in effectively and efficiently securing their data and IT systems with Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP).
Employees are increasingly using cloud services. Also cloud services that are not officially approved by their IT department, also called Shadow IT. Shadow IT is on the rise.
With ARAMA TECH Cloud Services Security, companies can control Shadow IT. Customers keep control over the data they exchange with cloud services. ARAMA TECH Cloud Services Security works through a proxy in which the same policies that customers have defined for their network and endpoints are also applicable to Cloud services. This allows customers to use these cloud services, but at the same time take the same protection measures they have previously defined.
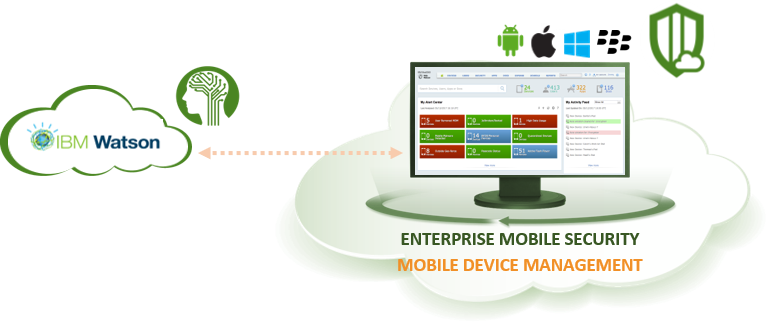
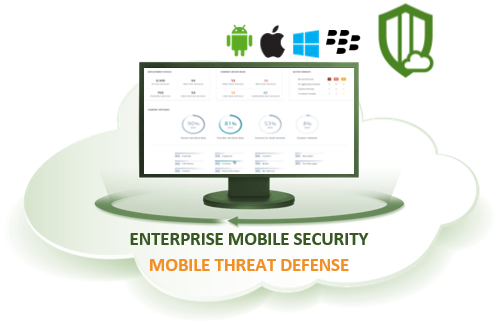
ARAMA TECH ENTERPRISE MOBILITY SECURITY
Mobile Device Management (MDM) powered by artificial Intelligence gives you more overview and control over IOS, MacOS, Android, Windows, and Blackberry devices, from one bundled cloud platform. ARAMA TECH MDM is powered by IBM Watson Artificial intelligence that enriches the management of your mobile devices with the world’s most advanced cognitive artificial intelligence system that allows the quality and security of managing your mobile devices is strengthened.
ARAMA Tech Mobile Device Management can be bundled and integrated with ARAMA Tech mobile Threat Defense, which allows you to create a fully fledged Enterprise Mobile Security platform and with peace of mind to provide your employees with access to the mobile world.
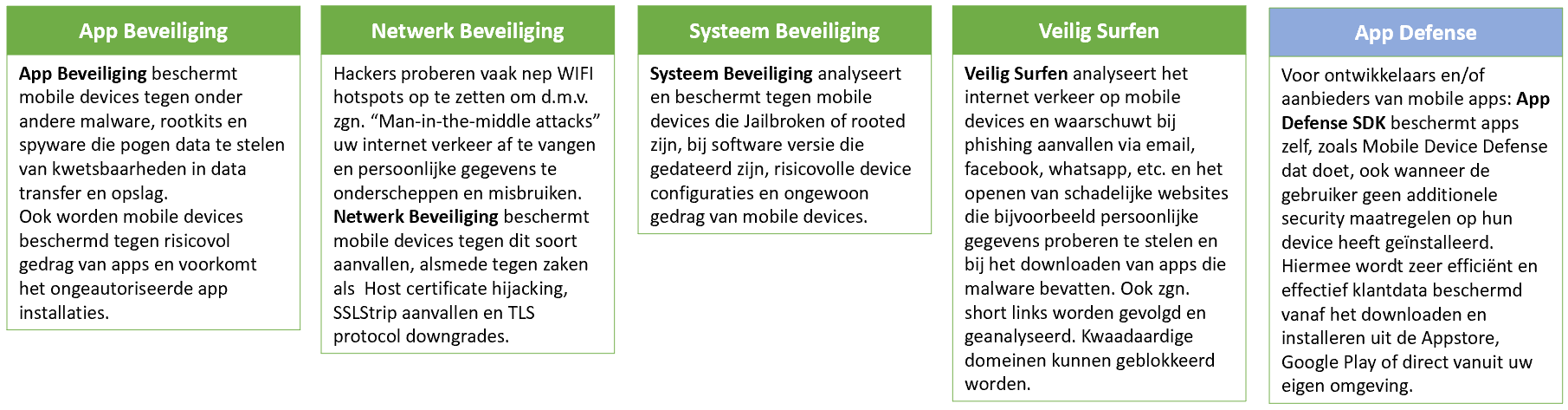
Cloud and mobility are becoming increasingly commonplace, and private and business smart phones and tablets are increasingly taking over computer functions. This makes mobile devices more and more interesting for hackers who attempt to exploit personal or business data or to inflict financial damage.
ARAMA TECH Mobile Device Defense provides protection for mobile devices through a lightweight endpoint app on the employees’ devices with a cloud-based admin console that provides real-time insight into mobile risks. ARAMA TECH Mobile Device Management can be bundled and integrated with ARAMA TECH Mobile Device Management to create a fully fledged enterprise mobile Security platform and with peace of mind giving your employees access to the mobile world.
ARAMA TECH’s Professional Services offers complete “end-to-end” Professional Services that are formed but not limited to Strategy and Roadmap design, Risk Assessment and Business Impact Analysis, Architecture & Design , Product sales and delivery, Technical & Business Implementation, Managed Security Services, Training & Education and Support.