Today’s threat landscape are generally pointing to terms Advanced Persistent Threats (APTs) and Advanced Targeted Attacks (ATAs). In reality there is a lot of overlap in the meaning of both terms so we call them Advanced Threats.
Advanced threats are a more sophisticated and concentrated effort, usually focusing on a single target, where the goal is to obtain sensitive and valuable information for financial reasons or corporate espionage. The trend is that Advanced Threats are targeting end users by preference.
These attacks often use previously unknown vulnerabilities, such as zero day attacks. They often develop over time and take months to unfold, while the attackers continuously monitor and extract data. In contradiction to other threats and attacks, Advanced Threats are usually performed by well-funded and good organized professionals.
How Do they work
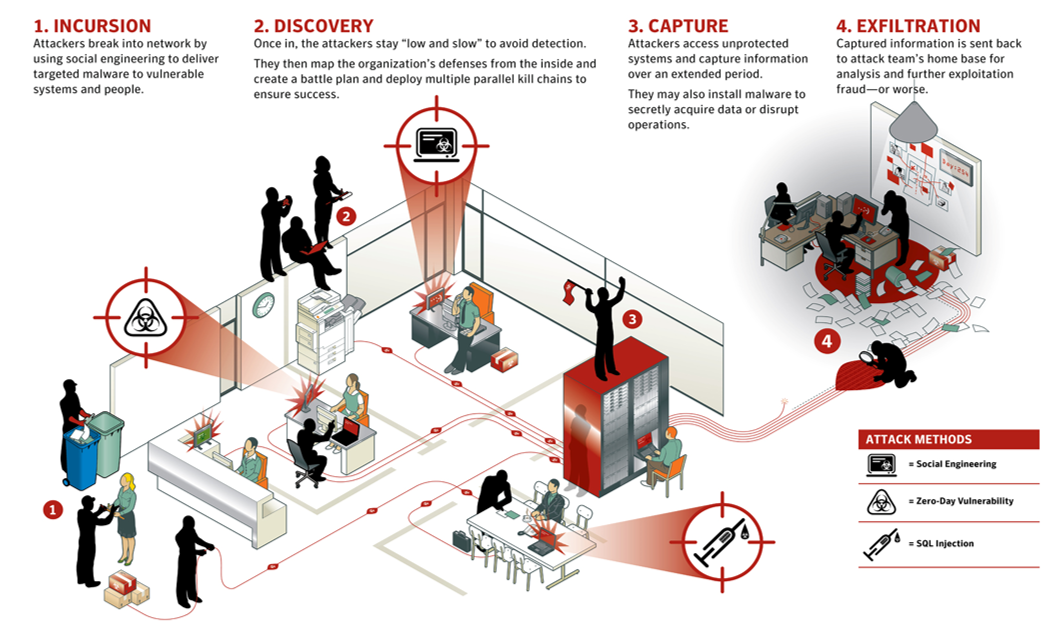
Advanced Threats are carefully planned and meticulously executed. They typically break down into four phases: incursion, discovery, capture, and exfiltration.
During the incursion phase, attackers often use a mix of social engineering, zero-day vulnerabilities and targeted malware to gain initial access to the organization’s network. Access is often gained through a lower priority system or one deemed to be of lesser importance than the final target.
Another frequently used attack vector is a spear phishing attack, which is an email attack designed to gather sensitive information and targeted at specific individuals within a company.
Once initial access is gained, the attackers seek to map out the organization’s systems and discover any vulnerabilities, credentials, or other possible access methods to the organization’s confidential and valuable data.
Once the systems have been mapped out and an attack vector identified, attackers move on to the capture phase. During this phase they access unprotected systems and capture information about the system over an extended period of time. They may also install malware in preparation for the next phase of attack.
During the final phase, exfiltration, attackers have seized control of the targeted systems and proceed with the theft of confidential and valuable data. Once the attackers have the data they can then proceed to further analyze and exploit it.
How to defend
Since Advanced Threats are multi-vector attacks, performed over a long period of time and are typically very stealthy, our defense needs to be sophisticated, thorough and well organized covering Protection, Detection and Response. Strategy and vision, supported by Security Intelligence, are needed to form the base how to address the risks organizations are facing today and tomorrow over Process, People and Technology. Preparation is the key word here: proactive security is absolutely necessary! If you don’t, the damage may be beyond any imagination. Examples of companies who went bankrupt after a successful cyber-attack are a realistic picture!
It is not a matter of íf they are coming, we knów they are coming, and we’d better be prepared for them!
